Autorize - Burp Extensions Series
This is Part 1 of a series that explores and showcases Burp Extensions which help our team during Web Application Security Assessments. These Extensions provide the necessary efficiency and effectiveness needed.
As the name suggests, Burp Extensions extend and customize the functionality of Burp in numerous ways, from something basic such as adding a custom scanner to check for retired libraries to something more advanced such as running custom python scripts when a request is being made (more on that in part 2!). There basically two types of extensions, the Community and the PRO extensions which require a professional license to be present when installing them.
Autorize is a free Burp extension that is authored by Barak Tawily. Autorize helps identify access control and authorization misconfigurations easily just by browsing the web application. You can find the extensions source code on GitHub.
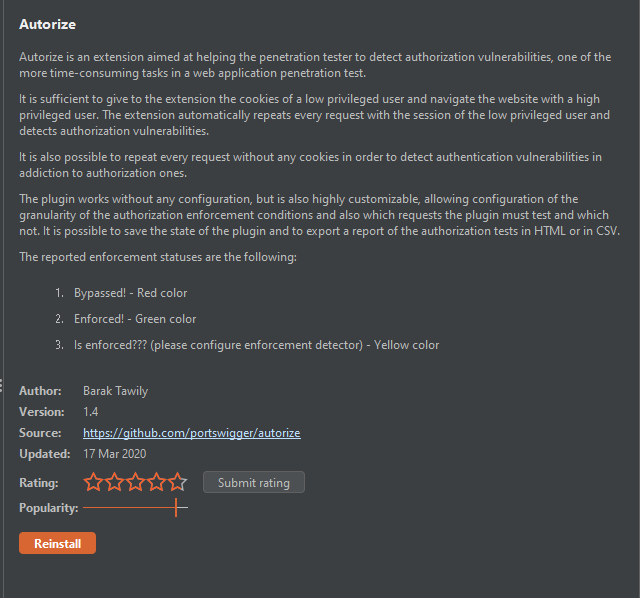
Example
To use Autorize a user cookie or an authorization header must be provided to the extension configuration with low user privileges. Next by browsing through the application with a higher privileged user, Autorize will replicate every request with the modified cookie or authorization header and compare the two responses to identify any misconfigurations.
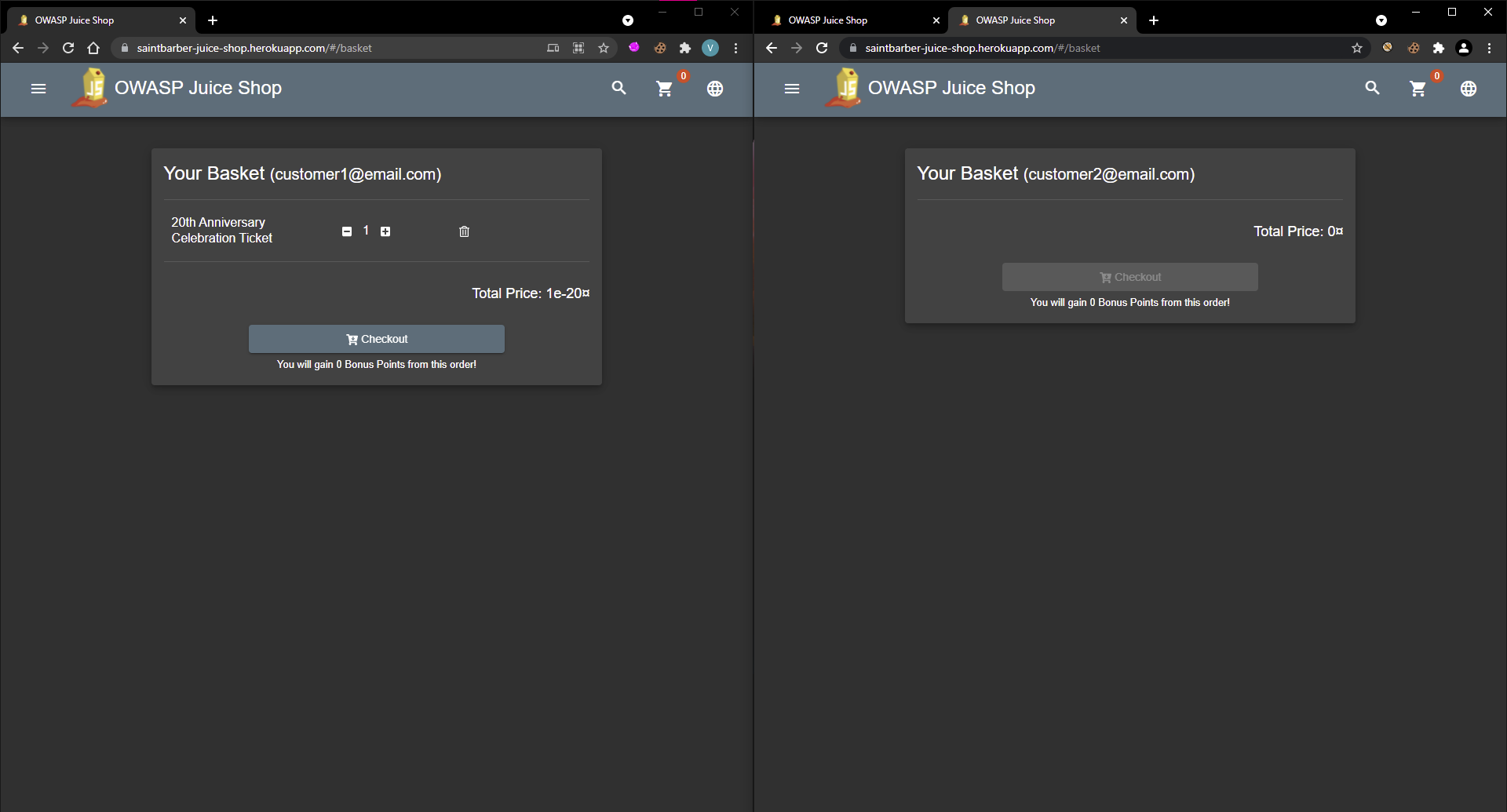
In our demonstration, the OWASP juice shop vulnerable web application will be used. A live example of the application can be found here. This example shows a Broken Access Control vulnerability with two users that have the same role This email address is being protected from spambots. You need JavaScript enabled to view it. and This email address is being protected from spambots. You need JavaScript enabled to view it., the same concept can be applied to higher and lower privilege users.
From the screenshot below the vulnerable application can be seen with the two users logged in.
By supplying the customer2's token in the Autorize configuration tab, the attacker can browse the site as customer1 and wait for the responses to be logged.
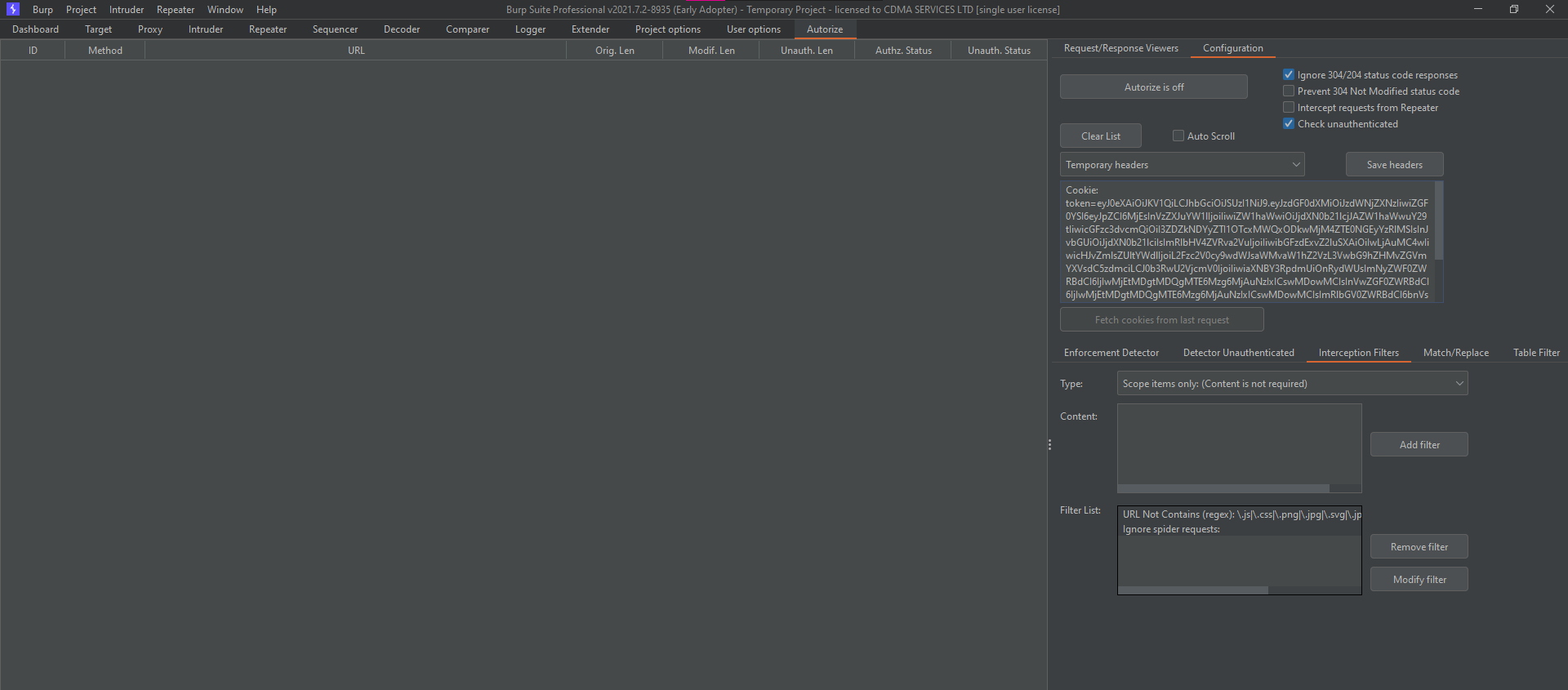
Autorize also has filters in the configuration tab where one can filter which responses matter most in the penetration test.
From the web application, the user can add an item to the customer1 basket, and then view browse to the basket. Autorize logs all requests in the left column as it can be seen in the following screenshot, the Authz. Status shows which endpoints can be accessed by customer2. The Unauth. Status shows unauthorized users, basically removing the cookie and any authorization headers entirely, this option can be removed by unchecking the Check unauthenticated option from within Autorize configuration tab.
One example of improper authorization can be found on the request with ID 195 which shows that the specific endpoint can be accessed by the customer2 user but has correctly implemented authorization for any unauthorized users.
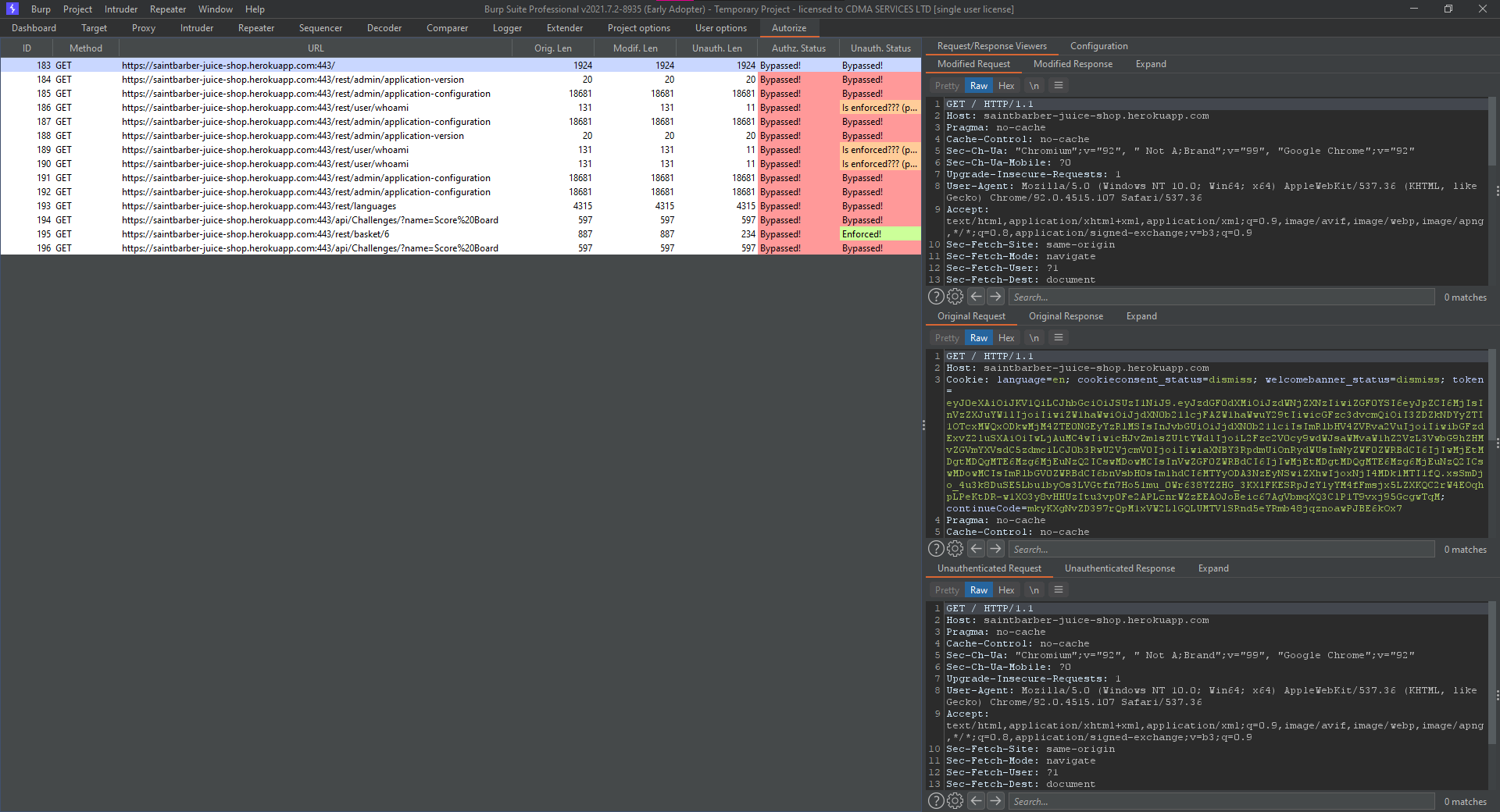
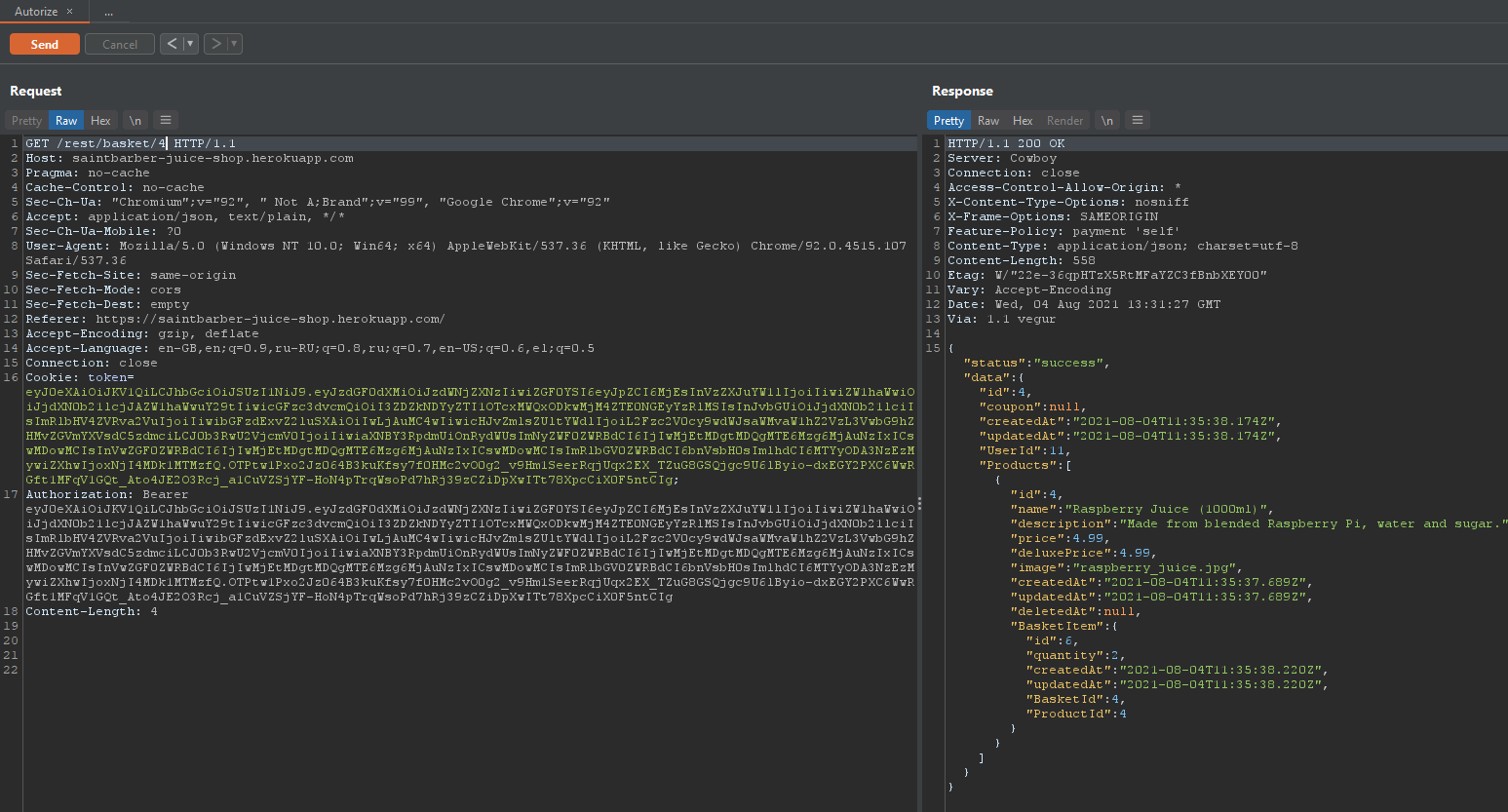
Notice below an attacker can access a different users basket (UserId: 11) by changing the request URL to /rest/basket/4.
As you can see, Autorize is a must-have extension for testing broken access controls and IDOR vulnerabilities.
In the coming weeks, our team will be posting other tutorials featuring Burp Extensions so stay tuned for that!

